Ultimate Hunter IO Review: Comparing with Other Email Finder Equipment
Wiki Article
Hunter IO Testimonial: Enhancing Your Email Look Performance
In the realm of digital interaction, efficiency is vital, especially when it involves email search and outreach. Seeker IO emerges as an encouraging option for improving this process, offering a suite of devices made to boost e-mail search effectiveness. From its Email Finder tool to Campaigns feature, Hunter IO presents a durable set of capabilities targeted at maximizing email-related tasks. What collections Seeker IO apart from various other devices in this field? Allow's check out how this platform can revolutionize your email search ventures and raise your interaction methods to new heights.Attributes of Seeker IO
One essential function is the Email Finder, which permits users to enter a domain name and get a listing of email addresses connected with that domain name. In Addition, Seeker IO offers Email Verifier, a device that assists individuals make certain the validity of e-mail addresses before sending out messages.Another valuable attribute is the Campaigns tool, which enables customers to arrange and track their e-mail outreach efforts efficiently. Individuals can create customized email projects, established automated follow-ups, and display feedbacks all within the platform. This function is especially valuable available specialists, marketing professionals, and recruiters who rely upon e-mail interaction to reach their targets.
Additionally, Hunter IO gives a Chrome expansion that integrates seamlessly with individuals' web browsers, enabling quick accessibility to email search abilities while surfing the web. This extension enhances customer experience by supplying on-the-go access to Seeker IO's functions without the need to switch over in between applications or tabs.
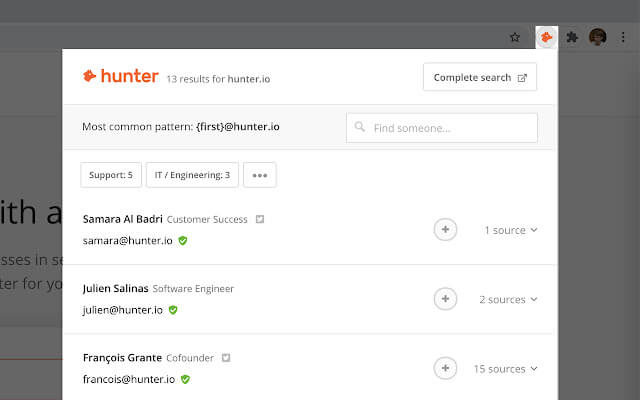
Exactly How Seeker IO Functions
Effectively promoting email search procedures, Hunter IO runs by leveraging sophisticated algorithms to scan domains and obtain appropriate email addresses connected with them. The system functions by permitting customers to input a domain name, following which Hunter IO's algorithms meticulously creep via the internet to remove e-mail addresses connected to that domain name. This scanning process is automated and swift, allowing customers to obtain exact get in touch with details efficiently.Moreover, Seeker IO uses various strategies to validate the precision of the removed email addresses, making sure a high deliverability rate. By cross-referencing data from several resources and utilizing domain name confirmation tools, Hunter IO boosts the reliability of the offered e-mail addresses. This confirmation process help individuals within their designated recipients successfully, thus enhancing interaction initiatives.
In Addition, Seeker IO supplies individuals the alternative to execute mass searches, allowing them to draw out several email addresses all at once. hunter io review. This feature is specifically helpful for specialists and companies who require call information for countless individuals or business. Generally, Hunter IO streamlines the email search procedure, making it a useful tool for improving efficiency and performance in reaching out to get in touches with
Benefits of Using Hunter IO
Enhancing email search capabilities with advanced formulas and effective procedures, utilizing Hunter IO offers a plethora of advantages for users in various industries. Among the crucial benefits of making use of Hunter IO is Source its time-saving function. By automating the email browsing procedure, individuals can promptly access relevant call information without spending hours manually combing the web. This efficiency not just why not try this out conserves time but additionally raises efficiency by allowing individuals to concentrate on various other vital jobs.In Addition, Hunter IO offers a high degree of precision in its e-mail search engine result. The system's sophisticated algorithms make certain that the given e-mail addresses are valid and up-to-date, reducing the possibilities of jumped emails or stopped working distributions. This reliability is crucial for preserving a favorable sender track record and ensuring that essential interactions reach their desired recipients.
Additionally, Seeker IO improves outreach strategies by giving users with valuable insights right into their target market. By gaining accessibility to accurate call details, services can tailor their email projects better, leading to enhanced engagement and greater conversion rates. In general, the advantages of utilizing Hunter IO prolong past easy email search abilities, offering users a thorough remedy for maximizing their interaction initiatives.
Combinations With Hunter IO
Incorporating Seeker IO with various platforms and devices improves the overall performance and performance of email search processes for customers. By seamlessly integrating with popular platforms like Google Sheets, Salesforce, and HubSpot, Seeker IO permits individuals to straight access its email searching for capacities within these devices. This assimilation simplifies the workflow, removing the demand to switch between numerous applications and saving important time. Seeker IO's API assimilation allows users to automate the email search process, making it more convenient and decreasing manual efforts.In addition, incorporating Seeker IO with outreach tools like from this source Mailshake or Outreach.io enables customers to flawlessly incorporate validated email addresses right into their campaigns, enhancing the chances of reaching the best audience effectively. In general, these combinations boost the functionality of Seeker IO and maximize email search processes for customers across numerous industries.

Pricing Choices and Strategies
Amongst the vital factors to consider for customers reviewing the Seeker IO service is the variety of pricing alternatives and strategies available - hunter io review. Seeker IO supplies a selection of plans customized to match different customer requirements, ranging from the Free plan, which supplies restricted accessibility to functions, to the Business plan, offering considerable performances for larger companiesThe Free plan enables individuals to carry out as much as 50 complimentary searches each month, making it suitable for individuals or small organizations with periodic email search needs. For advanced attributes such as bulk searches, e-mail confirmation, and access to additional information points, users can choose the Beginner, Development, or Pro strategies, which supply increased search limits and enhanced abilities.
For business looking for a thorough e-mail search option, the Business plan gives personalized prices based upon details requirements, including API gain access to, devoted support, and progressed features for effective e-mail outreach projects. By using a range of rates choices and plans, Seeker IO makes certain that customers can select a bundle that aligns with their spending plan and use demands.
Conclusion
In conclusion, Seeker IO uses a detailed solution for improving email search efficiency via its powerful functions, advanced algorithms, and smooth combinations. By automating the procedure of finding and validating email addresses, Seeker IO conserves time and boosts outreach methods for individuals. With numerous pricing plans to match different needs, Hunter IO is a useful device for maximizing interaction efforts and improving performance in e-mail search tasks.The attributes of Hunter IO supply individuals with valuable tools for enhancing e-mail search efficiency. One key attribute is the Email Finder, which permits users to enter a domain name and get a list of e-mail addresses associated with that domain name. In Addition, Seeker IO uses Email Verifier, a device that assists customers make certain the legitimacy of email addresses prior to sending out messages.Effectively promoting e-mail search processes, Seeker IO runs by leveraging sophisticated algorithms to scan domain names and fetch pertinent e-mail addresses linked with them. The platform's innovative algorithms ensure that the supplied e-mail addresses are legitimate and up-to-date, lowering the opportunities of jumped e-mails or failed distributions.
Report this wiki page